Cisco ACI bring a scalable model to being able to enforce wire rate security on any port to leverage a state checking packet filter for application traffic. Historically this was not viable from a management perspective due to the need to associate every filter with an IP address, which is solved with the group based policy model. But it also wasn’t viable because security teams don’t just want to kill packets. They want to see them die. They are that kind of people.
And this ability to provide adequate visibility for dropped traffic was the reason for passing ALL traffic through an expensive stateful firewall device. If you want to protect a web server on port 80 and 443, why do you want to invest expensive resources on all the traffic you just want to drop? The reason was this visibility it provided. The security teams want to see people knocking on the front door.
This Nexus 9000 family has the ability to provide this functionality, today. It is the first System on chip switch (read: Super high scale, low latency, attractive cost point), that is capable of providing full visibility of every packet of every flow. It can do this via incorporating with Tetration analytics and Cisco Stealthwatch. Now with this visibility, it is possible to scale your expensive stateful resources to only focus on the traffic that is important to them, dropping the uninteresting traffic in the line rate fabric, without compromising on visibility.
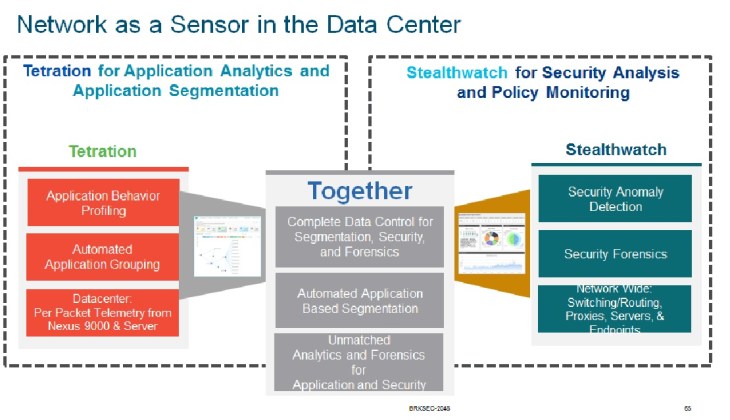
Stealthwatch + Tetration : Better together
Cisco acquired Lancope for one purpose, they had hands down the best security analytics that could be applied to netflow traffic. Think about that, any router you had already purchased, that is depreciating in the network, can now be a sensor with stealthwatch providing the security analytics to see what is going on in the network, whether it is campus, data center, or branch. Because all traffic goes through the network, and when you turn the network into a sensor, you get full visibility of all traffic.
In addition, organizations who are moving to cloud and new data center models are needing to have better understandings of their application dependency mappings in order to componentize the applications and make them cloud native. To do this, you can’t just understand the application (port 80, 443), but also everything else the server is providing. So your web application may only listen on port 80 and 443, but likely uses an authentication infrastructure. And you probably back it up (hopefully), and are certain to patch it, may need to ssh into it, and syslog/ntp, other services it relies on, need to be fully understood. Tetration handles this visibility. It can go into a network and understand all traffic that is going on in support of an application, apply machine learning to create application dependency mapping, determine normal traffic, and even group like applications to provide insights you never anticipated.
And now, these two tools are able to work together, and as time goes on, they will get even more symbiotic in nature. For example, Tetration can provide application dependency maps from which Stealthwatch can correlate normal versus anomaly traffic. This is the visibility your network teams need to entrust using the line rate resources currently laying fallow in your network (you bought all that ACL tcam…), and turn it into a line rate stateless firewall to properly scale your expensive stateful resources and use them for what they are best at : Protecting your key applications through best in class security tools.